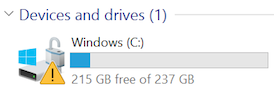

Thinking it might have something to do with encryption, I searched Settings for "BitLocker" and was directed to System > About where I found this:
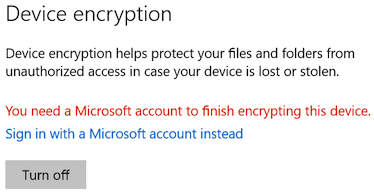
You need a Microsoft account to finish encrypting this device
Hardly believing such a thing was possible, I turned to the Internet for answers; sadly, Microsoft confirmed the ugly truth (highlighting and missing comma added):
Unlike a standard BitLocker implementation, device encryption is enabled automatically so that the device is always protected ... If the device is not domain-joined, a Microsoft Account that has been granted administrative privileges on the device is required. When the administrator uses a Microsoft account to sign in, the clear key is removed, a recovery key is uploaded to online Microsoft account and TPM protector is created. Should a device require the recovery key, the user will be guided to use an alternate device and navigate to a recovery key access URL to retrieve the recovery key using their Microsoft Account credentials.
Cem Paya clarifies it rather succinctly:
Remembering that "not domain-joined" will apply to most consumer PCs for use at home, this translates to: for any Windows 8.1 machine that happens to have requisite TPM hardware, BitLocker disk encryption will be enabled with recovery keys escrowed to MSFT automatically.
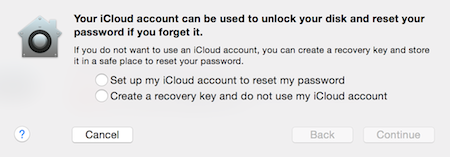
At least Apple still has the decency to ask (for now?) if you want to give them your recovery key:
More information and updates:
/windows | Sep 21, 2015