Patrick Wardle highlighted a tweet by Maxwell ("Some Apple apps bypass some network extensions and VPN Apps. Maps for example can directly access the internet bypassing any NEFilterDataProvider or NEAppProxyProviders you have running"), sparking an extensive HN discussion on Apple's ham-fisted tactics (not unlike Google's recent behavior).
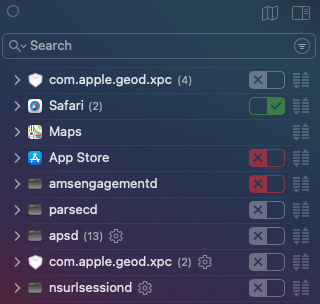
A search for "NEFilterDataProvider" turned up David Dudok de Wit's post fingering the ContentFilterExclusionList key in /System/Library/Frameworks/NetworkExtension.framework/Versions/A/Resources/Info.plist as the culprit. The default list includes 56 Apple apps and daemons like App Store, MusicLibrary, softwareupdated, etc.:
Deleting those entries under Big Sur turned out to be rather involved; in fact, one could be forgiven for coming away with the vague suspicion that Apple would prefer them not to be disturbed:
Disable FileVault
Boot into macOS Recovery, disable SIP (csrutil disable) and SSV (csrutil authenticated-root disable), and reboot
Find the root mount device, e.g.,
% mount
/dev/disk1s5s1 on / (apfs, local, read-only, journaled)
...
% mkdir mnt
% sudo mount -o nobrowse -t apfs /dev/disk1s5 mnt/
Edit Info.plist as desired, e.g., % sudo vi mnt/System/Library/Frameworks/NetworkExtension.framework/Versions/A/Resources/Info.plist
% sudo bless --folder mnt/System/Library/CoreServices --bootefi --create-snapshot && sudo reboot
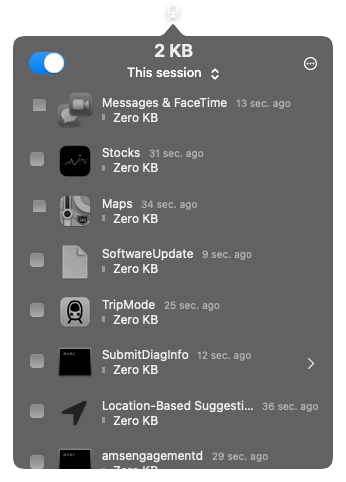
Little Snitch 5 and TripMode 3 had no problem blocking the previously-cloaked processes afterwards:


though one may well be left with a niggling doubt: should all this really be necessary to monitor your own computer's network traffic?
UPDATE 1: Hany, author of Murus and Vallum, was kind enough to reply with some testing of his own:
I did some tests and I’ve found at least one major issue on Catalina.
Removing all entries from the dictionary key seems to work for most listed processes: connections are seen by the network filter and flows are passed/blocked according to matched rules. But it does not work for at least one of the listed processes: IMTransferAgent. If you use macOS Messages.app then you may be aware that this process is used to send messages attachments.
If removed from the list, the process is always blocked. The filter provider does not see any flow for that process, and any attempt to send attachments with Messages.app will fail until you disable the filter.
UPDATE 2: The traffic of some Apple processes isn’t shown in Little Snitch 5.
UPDATE 3: Enabling Little Snitch 4.6 kext under Big Sur
UPDATE 4: Tweet by Apple developer Russ Bishop: "Some system processes bypassing NetworkExtensions in macOS is a bug, in case you were wondering." and some replies:
UPDATE 5: Exclusions Blaster
UPDATE 6: Hooray, no more ContentFilterExclusionList
/mac | Oct 21, 2020