with RetroTick (GH | HN):
"Run classic Windows and DOS executables directly in your browser. No installation required. Just drag, drop, and watch programs come alive in a web page.
"RetroTick is an x86 virtual machine and Windows/DOS API compatibility layer built from scratch in TypeScript. It parses PE (Win32), NE (Win16), and MZ (DOS) binaries, executes x86 machine code instruction by instruction, and reimplements a subset of the Win32, Win16, and DOS API surface, enough to boot several .exe files from the classic Windows era and render their GUIs in the browser."
The demo site offers a host of classics to enjoy:
- Games
- Cards (DLL)
- FreeCell
- SkiFree
- Solitaire
- Minesweeper
- Programs
- Calculator
- Clock
- Command Prompt
- GLX Gears
- MS-DOS QBasic
- Sound Recorder
- Super PI
- Task Manager
- Welcome to Windows 95
- Screen Savers
- 3D Maze
- 3D Pipes
- Bezier
- Flower Box
- Marquee
- Mystify
- Starfield Simulation
Updates
The developer shared on HN: "Hidden feature: right-click any executable and select 'View Resources' to browse its embedded resources like icons, bitmaps, dialogs, and version info. It even supports viewing Delphi forms (though Delphi programs can't actually run yet). Think of it as a browser-based Resource Hacker or eXeScope."
retrowin32 "is a still-early Windows emulator for the web (and other non-Windows platforms). Take a win32 .exe file and run it in a web browser or a Mac. See some demos."
❧ 2026-02-27
Despite billing itself as a "vibrant community", the Apple Support Community (aka Apple Discussions) apparently does not tolerate dissent.
A Google search turned up iOS 26.2 (and all of 26) worst upgrade ever hosted on Apple's discussion forum:
Clicking the link redirected to a login page, which was unusual, but OK:
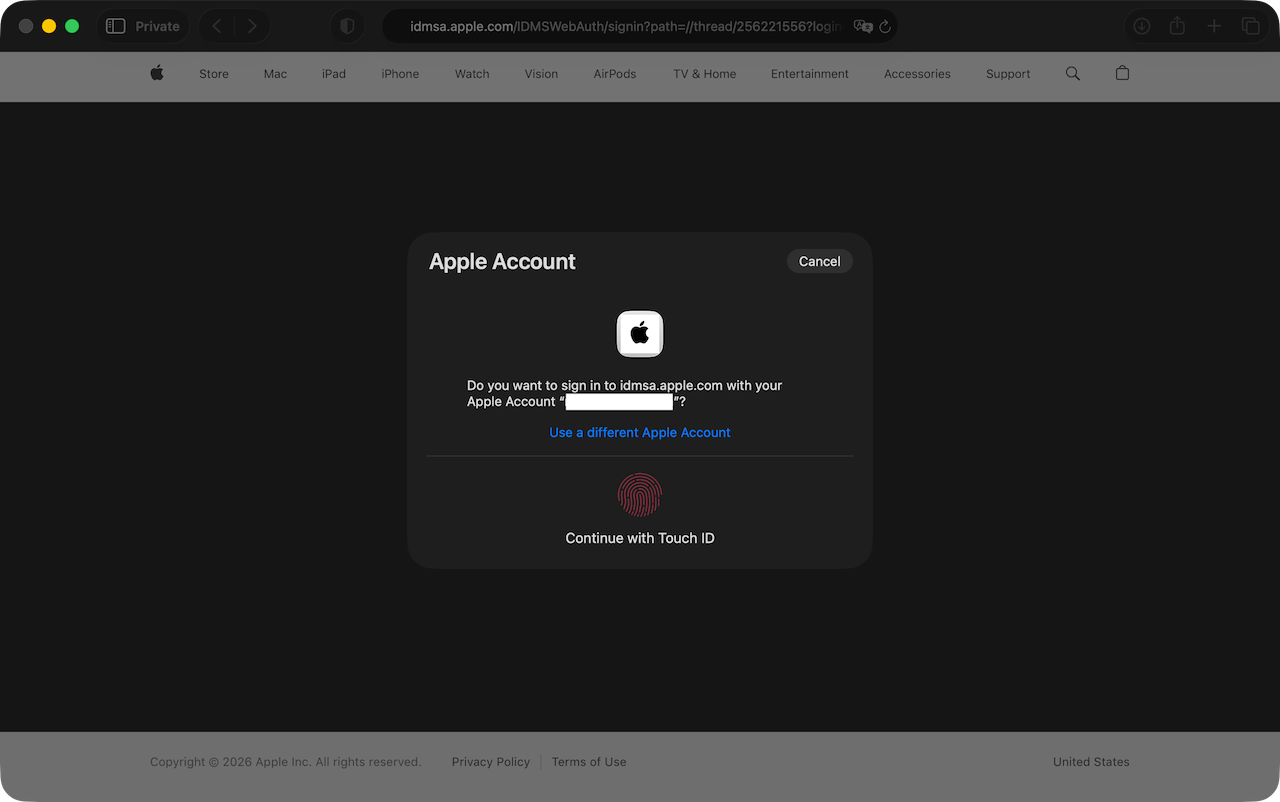
That led to an Access Denied page (despite other discussion pages remaining accessible):
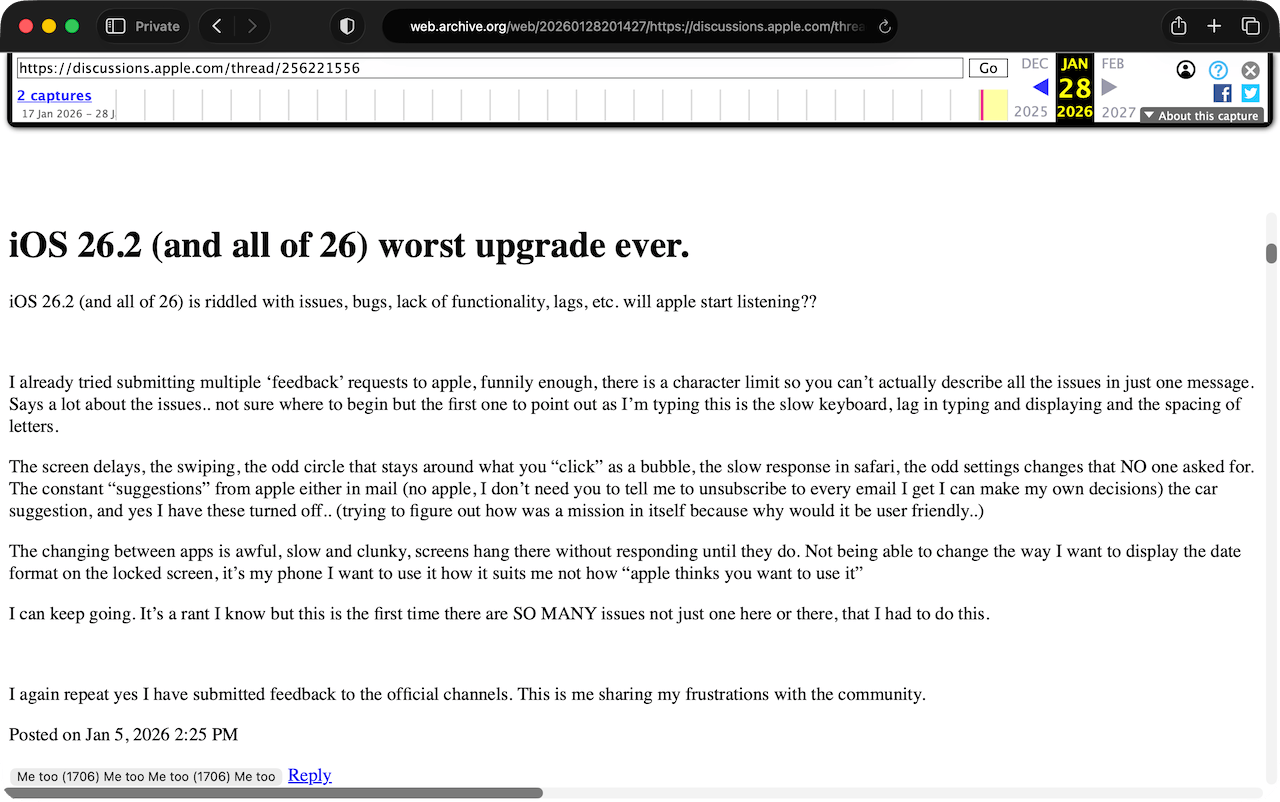
Happily, the Wayback Machine had a copy; it showed 1,706 "Me too" votes just 23 days after the post was made:
Apple isn't having quite as much luck censoring the rest of the web:
❧ 2026-02-14
iOS 26.2 broke MileBug at last; it hadn't been updated in years, the founder having apparently sold to Bending Spoons in 2018. Failing to find a simple mileage tracker in the App Store, I cobbled together a Shortcuts workflow which does the job.
Starting mileage is automatically populated by the previous ending mileage, though it can be quickly adjusted via the dashboard widget when necessary (as when switching vehicles or having driven untracked miles).
1. Setup
Create the Log Database
- Open Notes.
- Create a new note titled
Mileage Log.
- Add this header on the second line:
Date,Vehicle,Start,End,Mileage.
Create the Storage Folder
- Create a new folder in Notes named
Mileage.
Create the Tracker Note
- Inside the
Mileage folder, create a new note titled Milebug.
- Enter your current odometer reading on the second line (immediately under the title).
Configure a Dashboard Widget
- Add a Notes widget to your Home Screen, swiping to select one of the Folder options (as opposed to "Note" or "Quick Note"), then tap Add Widget.
- Tap the widget while it is still jiggling and change the Folder setting from the default
Notes to Mileage.
Configure System Settings
- Navigate to Settings → Apps → Shortcuts → Advanced.
- Enable Allow Deleting Without Confirmation. (Ensures that the shortcut runs silently in the background without prompting you every time it updates the tracker).
2. Shortcuts workflow
Open the Shortcuts app and tap + to create a new shortcut.
2.1. Vehicle Selection
- Add List.
- Rename the default items (
One, Two) to your vehicle names (e.g., FJ40, Fit).
- Add Choose from List.
- Add Set Variable.
- Set Variable Name to
Vehicle.
2.2. Get Start Mileage
- Add Find Notes.
- Add Filter → Name contains
Milebug → Limit to 1 item.
- Add Get Text from Input.
- Should automatically connect to
Note.
- Add Split Text.
- Should auto-fill New Lines.
- Add Get Item from List.
- Change
First Item to Item at Index 2
- Add Set Variable.
- Change
Variable Name to Start
2.3. Get End Mileage
- Add Ask for Input.
- Change
Text to Number.
- Change
Prompt to End Mileage.
- Add Set Variable.
- Change
Variable Name to End
2.4. Calculate Distance
- Add Calculate.
- Change + to -.
- Tap
Number and select Start from the list of options
- Add Set Variable.
- Change
Variable Name to Distance.
2.5. Prepare Log Entry
- Add Date. (Defaults to Current Date)
- Add Text.
- Tap inside the text box
- Tap the following tokens in the popup menu, adding a comma between each one:
Date, Vehicle, Start, End, and Distance.
- Tap the
[Date] token in the text box then set Date Format to Short and Time Format to None.
2.6. Save the Log
- Add Append to Note.
- Tap
Text and select Text token with yellow icon
- Tap
Note and select Mileage Log
2.7. Update the Tracker
- Add Find Notes.
- Tap
Appended Note then Clear Variable
- Tap Add Filter → for Name contains, change
anything to Milebug and limit to 1 item
- Add Delete Notes.
- Add Text.
- Tap inside the text box and enter
Milebug on the first line, press Return, then select the End variable from the popup menu
- Add Create Note.
- Change
Contents to the Text token with yellow icon
- Change
Folder to Mileage
3. Wrap-up
Tap the arrow next to the shortcut name at the top of the screen to access Rename, Choose Icon, and Add to Home Screen options.
Screenshot of the complete workflow.
To resolve access or permissions issues, tap the ⓘ button on the shortcut and check Privacy settings.
Related
Aidas kindly wrote in to recommend Juan Manuel Merlos' Open GPX Tracker. From the GitHub repo README:
"Open GPX Tracker is a GPS logger for iOS (iPhone, iPad, iPod) with offline map cache support. Track your location, add waypoints and send your logs by email as GPX files.
"This app has no annoying time restrictions, no ads and no in-app-purchases. You can create unlimited GPX traces :).
"If you are goint to track without Internet... don't worry! Before you go offline, browse the area where you'll be tracking and it will be cached and available offline.
"We care about your privacy, all the data recorded using the application is kept in your phone (or in your iCloud), wherever you store it. The app does not share any GPS data with us or any other 3rd pary. For more information see the Privacy Policy."
Shortcuts Toolkit: "Comprehensive toolkit for generating Apple Shortcuts programmatically using reverse-engineered binary plist format."
Shortcut Source Tool:
"Copy and paste multiple actions, view/edit/compare/save/import/repair/web-review shortcuts. ... Web Review can also be converted to and viewed/saved as plain text.
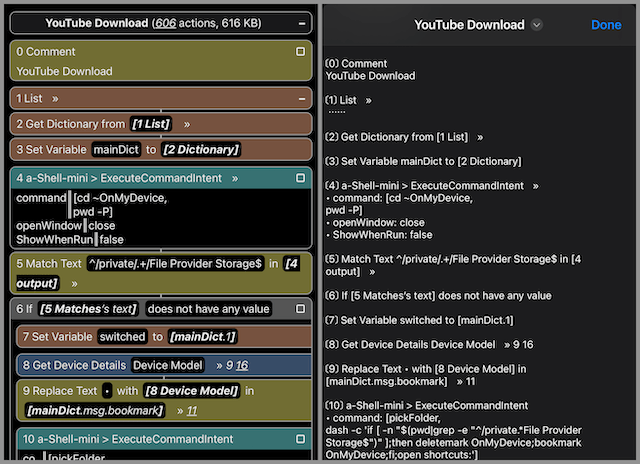 "
"
❧ 2026-01-30
Primarily aimed at local contacts, since cloud-synced contacts can be removed from the device by disabling contact syncing. Back up first; deletions are permanent.
Two-finger drag to multi-select contacts, then long press the selection to open the context menu and tap "Delete Contacts". Tedious for more than a few dozen.
This free (no IAP) app deleted over 43,000 contacts in a minute or two: Delete → View all contacts → More (⋯) → Select all → Delete Selected → Delete contacts
Shortcuts lacks a native "Delete Contact" action, but Scriptable (free; donations accepted via IAP) allows you to interact directly with the iOS Contacts API, e.g.,
Update
See also Delete all iOS contacts using the Contacts.framework.
❧ 2026-01-30
A. L. Wies (@DrogenDiego) has married an M1 MacBook Pro with a 40Hz color e-paper display from OED (one of E Ink's few competitors):
"I wanted to share my InkBook. It's a E-Paper Laptop. I bought a used 16 inch MacBook Pro M1 that had a broken screen and replaced it with an OED 13 inch color E-Paper Panel.
"It is based on the modos Paper Dev Kit that's available on https://www.crowdsupply.com/modos-tech/modos-paper-monitor
"I adapted the firmware to my needs and wrote custom dithering algorithms. Mine is using edge aware bayer dithering for most of the content. I also show floyd steinberg error diffusion dithering. It looks very natural but looses brightness.
"I put a thin 6 mm wooden case behind the display to fit the PCB. But with a custom PCB it would've been possible to include everything in the display case.
"It's connected via USBC and acts as an external display. I managed to keep the front camera working :)
"I will do a seperate video where I explain in detail how I did it and the steps involved.
"This year is gonna be really cool for E-Paper. The technology is ready now for everyday E-Paper screens.
"if you have questions you can write in the comments. I will answer them ;)"
A far cry from 2012!
❧ 2026-01-27
Email OAuth 2.0 Proxy is a local IMAP/POP/SMTP proxy that adds OAuth 2.0 authentication transparently, allowing email clients that don't support OAuth to keep working unchanged. From the README:
"Email services that support IMAP, POP and/or SMTP access are increasingly requiring the use of OAuth 2.0 to authenticate connections, but not all clients support this method. This tool is a local proxy that intercepts the traditional IMAP/POP/SMTP authentication commands and transparently replaces them with the appropriate SASL (X)OAuth 2.0 commands and credentials. Your email client, app or device can continue to use the login or auth/authenticate options, with no need to make it aware of OAuth's existence. The proxy works in the background with a menu bar/taskbar helper or as a headless system service, and is compatible with macOS, Windows and Linux. It can be used with any email provider that supports OAuth 2.0 authentication, including Outlook, Office 365, Hotmail, 21Vianet, Gmail, Google Workspace, Fastmail, Yahoo, Comcast, AOL and many others."
❧ 2026-01-06
Needing a Mac Pro (2019) power supply, I started at Apple's Self Service Repair Store.
Only the Mac Pro (2023) PSU was listed, so I clicked Find Out About Self Service Repair, which states that "Genuine Apple parts can also be purchased from a Genuine Parts Distributor":
"To repair Apple products, purchase genuine Apple parts from a Genuine Parts Distributor and reference the repair manual for your device.
...
"In the United States, parts can be purchased from this Genuine Parts Distributor:
"A Genuine Parts Distributor may require account creation or sign-in prior to order placement. See the distributor’s site for more information."
Not finding the part listed on MobileSentrix, I clicked the prominent chat bubble and asked whether it was available. I was informed that:
"At this time, in order for us to assist you with sourcing this part, you would first need to create an account with us. Since we operate on a B2B basis, we require valid business documentation to verify your account. Unfortunately, without this verification, we are unable to assist with sourcing the Mac Pro (2019) power supply."
No problem; I am a business customer and happy to create an account (though the B2B requirement seemed a little odd in light of Apple's "To repair Apple products, purchase genuine Apple parts from a Genuine Parts Distributor and reference the repair manual for your device."):
"Thank you for your understanding, and I appreciate your willingness to set up an account. Once you have completed the account setup, please return to this thread and let us know. We will be more than happy to assist you with sourcing the Mac Pro (2019) power supply and any other parts you may need."
Great! Set up the account as requested and was then informed:
"Please send your business license and government-issued ID to our onboarding team. Once your account is approved, we can proceed with sourcing the part for you. Please keep us updated once approval is complete."
I asked why a personal government-issued ID was required for a corporate account and was told that it "is a required part of the onboarding process even for corporate accounts."
OK, redacted the most sensitive bits on my driver's license with Preview and watermarked via iWatermark+ (for what it's worth), then sent along with the business registration.
Five days later, received this message:
"Thank you for sending over the requested documents. Unfortunately, we are strictly business to business wholesale suppliers who only service established brick and mortar phone repair shops. Due to this, we are unable to have your account approved. I apologies [sic] for any inconvenience that this may cause you"
True, my business does operate exclusively onsite and remotely; it might've been nice for Apple or MobileSentrix to mention a brick-and-mortar store requirement somewhere along the way before submitting sensitive documentation.
If only I had read Replace the power supply in your Mac Pro (2019) more carefully; it clearly states, "If you need to order a replacement power supply, contact Apple." Sure enough, they happily sold me the unlisted PSU by phone, no waiting, ID, or business documentation required!
❧ 2026-01-03
without installing kernel extensions or weakening system security, via anylinuxfs. Built on the libkrun microVM hypervisor and NFS, it provides read/write access to virtually any Linux-compatible filesystem (ext4, btrfs, xfs, ZFS, NTFS*, exFAT, etc.), encrypted volumes (LUKS, BitLocker), and advanced storage configurations (LVM, RAID, multi-disk setups). Works with internal/external drives, disk images, and GPT, MBR, or raw partition formats.
❧ 2026-01-01




 "
"